Risky Executables That Shouldnt Get Uploaded to a File Server
This article explains how to protect your website from malware upload past File Upload Form.
Statistics bear witness that file upload vulnerabilities are WordPress's third well-nigh mutual vulnerability type.
Hackers will oftentimes utilise file upload vulnerabilities to spread malware, gain access to web servers, perform attacks on visitors to a website, host illegal files, and much more.
This guide will place the gamble factors of having unrestricted file uploads before explaining the most mutual types of file upload vulnerabilities.
Finally, nosotros'll explicate how to secure the WordPress file upload organisation.
What are the take chances factors of unrestricted file uploads?
In that location are many take a chance factors associated with unsecured file upload systems including:
Server-side attacks
If a hacker successfully places an executable file on your server, they may use it to launch server-side attacks.
For example, if they upload a web vanquish, they may utilize it to take control of sure parts of your web server.
Exploiting file upload vulnerabilities too allows hackers to place trojan horses, viruses, and other malicious files on your website.
Triggering vulnerabilities in server applications or libraries
Uploading a malformed file or ane which masquerades every bit a different file type might trigger a vulnerability in certain pieces of server software.
One well-known assault exploited a vulnerability in the image processing software ImageMagick. Hackers discovered they could execute capricious code by hiding it inside prototype files that would exist processed past ImageMagick.
This would potentially allow the hacker to take command of the server.
Hackers may also upload files to trigger vulnerabilities in real-time monitoring software. There was a recent vulnerability in Symantec antivirus software that could be triggered by uploading a RAR file.
Triggering this vulnerability could event in memory corruption on the server, potentially crashing sure programs or the server itself. Hackers could besides use this file upload exploit to crash the real-time security monitoring, then perform another kind of attack.
Customer-side attacks
Uploading certain types of malicious files can make a WordPress website vulnerable to client-side attacks like cross-site content hijacking and XSS attacks.
Hackers might also be interested in uploading files that trigger vulnerabilities in the libraries or applications used by end-user devices. For example, there was a vulnerability in iPhone that caused a buffer overflow in LibTIFF.
Causing an administrator or webmaster to execute code
Malicious files including Windows viruses, Unix trounce scripts, and Excel files may exist uploaded if there are unrestricted file uploads.
A server ambassador or webmaster might discover these files, then open them to determine what they are — executing the code and allowing malware onto your server.
Hackers might exist able to deface the website
If your website publishes user-uploaded content, allowing unrestricted file uploads may result in your website existence defaced or used for a phishing attack.
The website's file storage organization may exist abused
Hackers ofttimes target unsecured file upload systems to store troublesome files. These files might include illegal software downloads, pornographic material, stolen intellectual property, malware, or information used by criminal organizations.
Hackers can learn more about the server
An incorrectly secured file upload form may display error messages that give hackers information about the server'southward configuration. This information might include file paths or folder permissions.
Causing denial of service attacks
Unsecured file upload forms may allow hackers to upload extremely big files or hundreds of files at in one case — performing a denial of service assault.
Types of file upload vulnerabilities
The almost common types of file upload vulnerabilities include:
Unrestricted file upload with the unsafe type
This vulnerability occurs in systems where any type of file tin can be uploaded to the server. It likewise occurs when the file type is not adequately verified by the server.
This vulnerability could let cybercriminals to upload any kind of executable file to the server.
In some cases, website owners might check the file extension of an uploaded file, but fail to verify that information technology matches the contents of the file which has been uploaded.

This allows executable code to be subconscious within files with different extensions.
To avert this vulnerability, the application must thoroughly cheque the files that are being uploaded and remove file types that can cause damage to the server.
The application should not rely solely on Content-Type HTTP header information when checking file types, but instead, use more detailed file checking processes.
Arbitrary file uploads
This vulnerability is created when a user is allowed to upload a file without beingness authenticated by the awarding.
The power to upload should exist restricted to authenticated users to forestall malicious individuals from uploading random files to your server.
Allowing arbitrary file uploads as well puts your site at greater adventure of a denial of service assail.
Uncontrolled resource consumption
Applications should identify restrictions on the size of files that can be uploaded and the number of files that can be uploaded.
Failure to exercise then can allow users to upload very large files or thousands of small files simultaneously, performing a DOS attack.
Files containing malware
If a website is parsing or inserting information from within an uploaded file, information technology may exist vulnerable to files containing malware.
This type of assault ofttimes uses SQL injection attacks or attempts to go the system to run another arbitrary piece of code.
Protecting your WordPress website from file upload vulnerabilities
Here are some simple steps yous can take to protect malware upload past file upload form.
Only allow specific file extensions
By default, WordPress allows registered users to upload many types of files. This includes various types of image, audio, video, and document files.
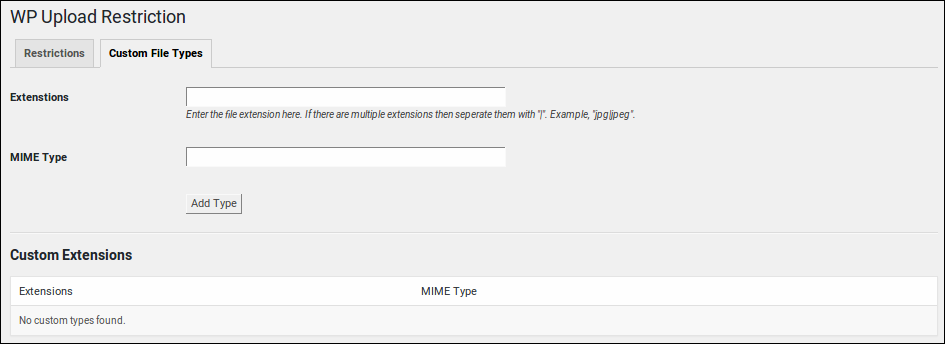
You tin reduce the types of files that users can upload by installing a plugin like WP Upload Restriction.
Use a WordPress form plugin that is secure
If you intend to accept file uploads on your WordPress website, choose a well-known file upload plugin that has splendid security. At a minimum, the plugin should safeguard your form against common grade attacks like Cross-Site Request Forgery (CSRF) and Cantankerous-Site Scripting (XSS) attacks.
Webmasters can also install a WordPress plugin that has real filetype detection, MIME analysis mapping, SVG sanitization, and a file upload debugger.
Such plugins make it easier to validate files and to create a whitelist of accepted MIME file types.
Reduce max file upload size
Preventing users from uploading large files will reduce the hazard of your file upload organization beingness used for a DoS attack.
There are multiple means to alter the maximum file upload size. The technique that works for y'all will vary based on your server configuration and permissions.
If you have complete control over your server environment, yous can alter the php.ini file to alter the allowed size of file uploads.
Open up your spider web server'southward php.ini file and modify theupload_max_filesize andpost_max_size directives. One time they have been updated, restart your HTTP server.

The snippet below volition change the maximum upload size to 4 megabytes.
You might also similar to include change themax_execution_time directive, which rejects an upload if it has taken too long to process. Some web servers will as well allow you to create a php.ini file in your website'southward home directory.
upload_max_filesize = 4M post_max_size = 4M max_execution_time = 120
Adding php upload values to your .htaccess
Some web servers will likewise let you to accommodate PHP file upload settings via the .htaccess file in your WordPress installation's root directory. Add the following to change upload sizes and max execution/input times:
php_value upload_max_filesize 4M php_value post_max_size 4M php_value max_execution_time 120 php_value max_input_time 120
Past default, WordPress doesn't permit public users to upload files. However, many WordPress administrators install plugins that contain file upload fields.
This is a potential vulnerability because you rely on the developer of that plugin to safely handle this content. Your website will be safer by only allowing certain types of registered users to upload files.
If you need a form with an upload field to just be displayed to certain users, apply a plugin similar to Restrict Content. Information technology volition permit you to restrict pages and portions of pages to certain types of users.
Add file execution restrictions using .htaccess
You can create a .htaccess file that restricts the types of files that tin can be executed from the uploads directory. For example, the post-obit .htaccess will only allow gif, jpeg, jpg, and png files to be executed:
deny from all gild deny,allow let from all
This .htaccess must not be placed into the wp-content/uploads directory, because hackers could potentially overwrite it by uploading some other file called .htaccess.
Place information technology in the directory above the uploads wp-content/uploads binder.
Place your uploads folder outside of the server root
Creating a new binder for storing uploads can also assist to improve file security. This folder should be created outside of your website'south public directory so hackers cannot manually execute the files they have uploaded via a website URL.
Read this short guide to acquire how.
Randomize uploaded file names
Once hackers have managed to upload an executable file to your server, they may try to execute information technology using a web browser or command line.
I unproblematic trick to preventing hackers from running their files is to randomly rename it. You tin read this curt guide to learn how to randomize uploaded file names in WordPress.
Don't give information away
If a user uploads a file that triggers an error, make certain WordPress and PHP only brandish a very elementary error message.
Avert displaying sensitive information like file paths, WordPress installation details, or server configuration information. This information could be exploited by a hacker.
Hackers will utilise many different techniques to obtain error messages from your website including uploading files that are in the wrong format, too big, or which have a very long filename.
Add a CAPTCHA to your forms
Adding the WordPress CAPTCHA plugin to your site prevents cybercriminals from using your forms for DoS attacks.
Force uploads to exist delivered in the correct file format
1 of the biggest issues with handling uploads is that hackers tin can hibernate executable code inside image file formats.
You lot tin can overcome this issue past forcing the webserver to send the correct image headers earlier you brandish an paradigm on your website.
For example, the following will force the prototype to be displayed every bit a png, ignoring whatsoever executable code:
$information = file_get_contents('/dwelling/potentially-dangerous-file.png'); header('Content-Type: image/png'); header('Content-Length: '. strlen($data)); header('10-Content-Blazon-Options: nosniff'); echo $data; Yous tin also process uploaded images using prototype manipulation software similar GD. By opening the image and re-saving information technology, you will remove any executable content.
Y'all tin can read more virtually security headers from the guide here.
Use a virus scanner on your server
Server-side virus scanners tin detect file uploads that contain malware, trojans, and viruses. The most mutual application for this task is ClamAV, an open up-source antivirus engine.
Make sure information technology is configured to automatically scan uploads that are added to your spider web server.
Nosotros hope this article volition assist you to protect your site from malware upload by file upload form.
Source: https://patchstack.com/articles/how-to-protect-site-from-malware-upload-by-file-upload-form/
0 Response to "Risky Executables That Shouldnt Get Uploaded to a File Server"
Postar um comentário